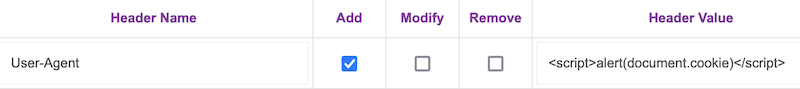
CVE NUMBER
CVE-2024-34899
SUMMARY
WWBN AVideo is a platform, written in PHP, engineered for the distribution of audio and video content, offering capabilities such as Video On Demand (VOD), streaming, and live streaming. To date, it has been installed on over 4,000 websites in more than 190 countries around the world.
A cross-site scripting (XSS) vulnerability has been identified in the view/about.php page of AVideo, affecting versions from 10.4 up to 12.4. This vulnerability can be exploited by sending a specially crafted request, which would result in the execution of arbitrary JavaScript code.
CONFIRMED VULNERABLE VERSIONS
The versions 10.4 up to 12.4 were tested and verified to be vulnerable by HDNA and confirmed to be vulnerable by the vendor.
PRODUCT URLS
AVideo - https://github.com/WWBN/AVideo
CWE
CWE-79 - Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’)
DETAILS
The PHP file view/about.php is vulnerable to an XSS issue due to no sanitization of the user agent.
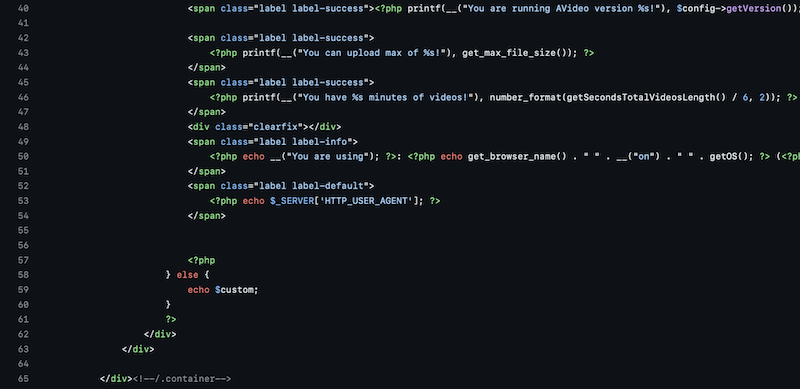
At line [53], the website gets the user-agent from the headers through $_SERVER['HTTP_USER_AGENT'] and echo it without any sanitization.
In PHP, echo a user generated statement, here the User-Agent Header, without any sanitization allows an attacker to inject malicious scripts into the output of a web page, which are then executed in the browser of anyone viewing that page.
POTENTIAL DAMAGE
The damage from such an attack can vary from minor nuisances to severe security breaches including session hijacking, account takeover, and data theft.
EXPLOIT PROOF OF CONCEPT
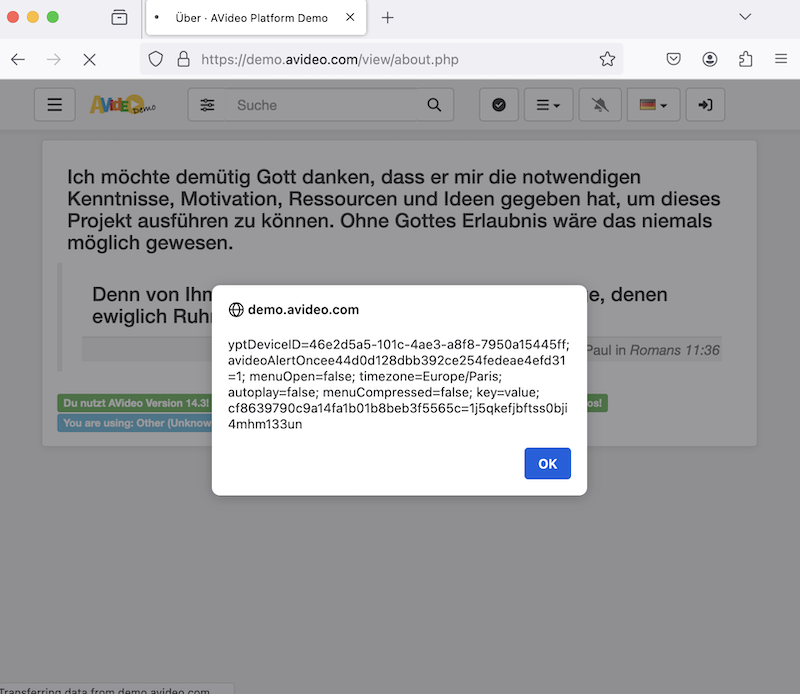
PUBLISHED FIX
AVideo commit 3457115 - https://github.com/WWBN/AVideo/commit/345711562621d879e63a817d01a229bf0aae7a1d
TIMELINE
2024-05-03 - Vendor Disclosure
2024-05-03 - Vendor Patch Release
2024-05-13 - Public Release
CREDIT
Discovered by HackerDna Research